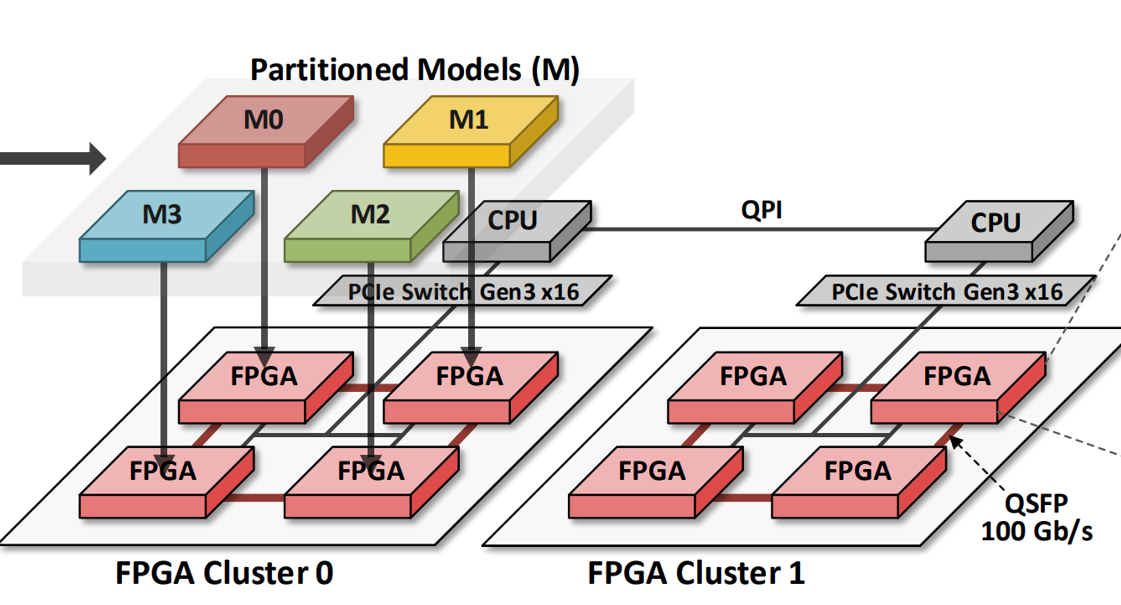
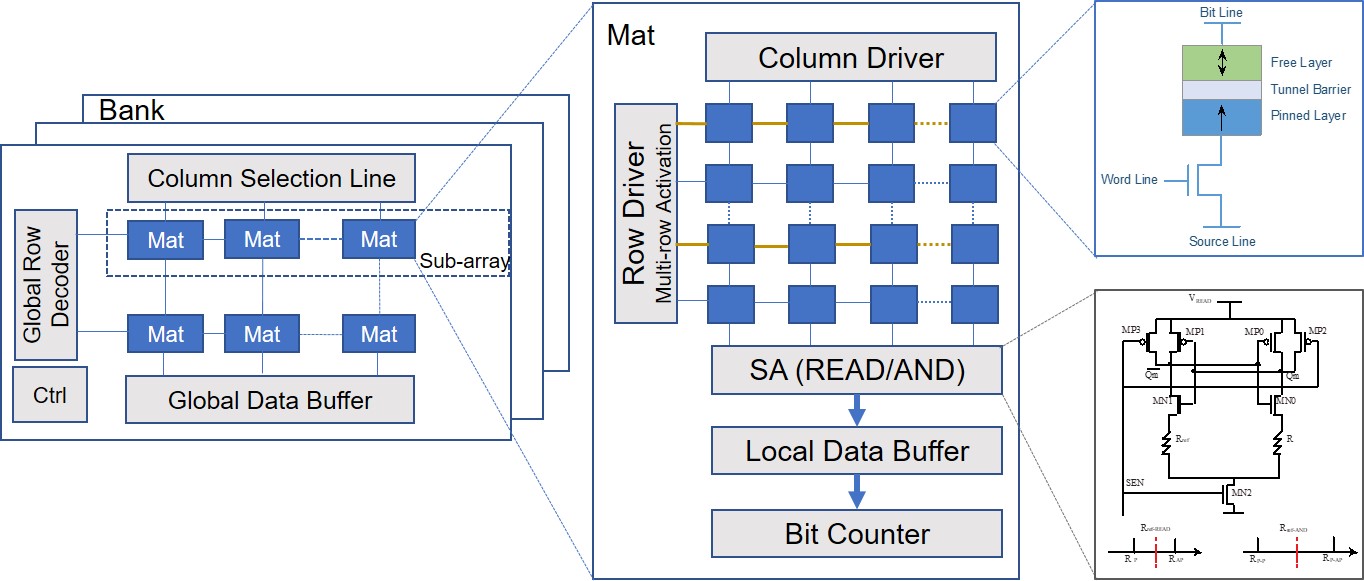
 | Chip Security
Chip security is critical in protecting integrated circuits from various threats such as hacking, counterfeiting, and reverse engineering. It involves implementing measures like secure boot, encryption, and hardware-based security modules to safeguard sensitive data and intellectual property. Techniques such as Physical Unclonable Functions (PUFs) provide unique identifiers for chips, enhancing authentication and anti-counterfeiting measures. Secure chip design also includes tamper detection and response mechanisms to prevent unauthorized access and modifications. Ensuring chip security is essential for applications in smartphones, IoT devices, financial systems, and military equipment, where data integrity and confidentiality are paramount.
|